Fighting SMS fraud: QR codes, shortlinks, and mobile apps
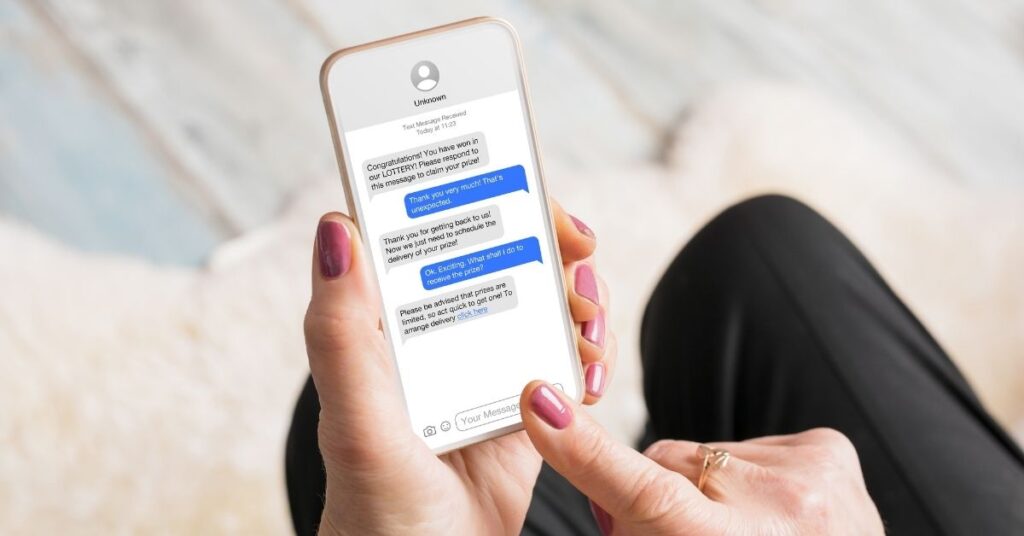
As businesses embrace the digital communication landscape, tools like Twilio and Messagebird have become indispensable. While these platforms empower genuine connections, they also pose a double-edged sword, susceptible to misuse for fraudulent purposes. One prevalent example involves the illicit use of Twilio in SMS-based scams.
Bad actors take advantage of Twilio’s capabilities to send seemingly legitimate text messages, deceiving recipients into divulging sensitive information or engaging in malicious actions.
These SMS-based scams often take on various forms, such as phishing attempts, where individuals receive messages that mimic official communication from reputable organisations. These fraudulent messages may request personal information, financial details, or login credentials under the guise of urgent account updates or security verifications.
What are the risks of communications platforms?
Platforms like Twilio and Messagebird offer great utility but can also be exploited by fraudsters. These bad actors create accounts mimicking reputable sources, like law firms or trusted companies, using them to execute scams. This form of digital impersonation can lead to significant financial and data security breaches.
As businesses and individuals increasingly rely on SMS for communication, understanding and mitigating the risks associated with Twilio-based SMS scams become paramount. Implementing robust authentication mechanisms, educating users about potential threats, and monitoring messaging patterns for anomalies are crucial steps in fortifying defenses against these deceptive practices. By staying vigilant and informed, users can harness the benefits of Twilio while minimising the risks posed by SMS-based scams in our interconnected digital landscape.
How do QR codes and shortlinks boost security?
QR codes have become essential in verifying the authenticity of digital interactions. When used in security-focused strategies, they serve as direct links to verified sources, ensuring clients engage with legitimate entities. Similarly, shortlinks provide secure and traceable pathways to genuine online destinations, reducing the risk of encountering fraudulent sites.
QR codes and shortlinks can play crucial roles in preventing fraud by enhancing security measures and providing efficient ways to verify information. Here are ways in which they contribute to fraud prevention:
Secure authentication
QR codes: Integrating QR codes into authentication processes adds an extra layer of security. They can be used for two-factor authentication, linking directly to secure login pages or authentication apps. Users can scan the code to confirm their identity, reducing the risk of unauthorised access.
Shortlinks: Shortened URLs can be employed in authentication workflows, enabling quick and secure access to verification pages. By shortening the URL, the potential for manipulation or phishing is reduced, as users are more likely to recognise and trust concise, branded links.

Mobile applications
Advanced mobile applications stand as a formidable defense. These applications, fortified with integrated security features, create a secure haven for transactions and interactions. Biometric authentication and real-time monitoring become the guardians of safety and authenticity in every exchange.
Within this robust ecosystem, innovative solutions like Checkboard seamlessly complement these security measures, further enhancing the overall resilience of mobile applications against evolving threats.
Educating consumers
An often-overlooked aspect of digital security is consumer education. Educating clients about the platform chosen by the firm for onboarding and communication is crucial. This includes:
Understanding the platform: Informing clients about how the chosen platform works, its security features, and why it’s safe. This knowledge empowers them to confidently use the platform and recognise legitimate communications.
Recognising official channels: Teaching clients to identify official communications, like genuine QR codes and shortlinks from the firm, helps them distinguish between authentic and fraudulent interactions.
Promoting vigilance: Encouraging clients to always verify the sources of communication and to use the secure mobile application for any sensitive transactions or data sharing.
Providing resources: Offering easy-to-understand resources, guides, and support for clients to familiarise themselves with the platform and its use in their interactions with the firm.
Why advanced security makes the difference
Advanced mobile applications stand as a formidable defense, fortified with integrated security features that create a secure haven for transactions and interactions. Biometric authentication and real-time monitoring become the guardians of safety and authenticity in every exchange.
Combining technological tools with client education for a united front against digital impersonation, QR codes and shortlinks ensure that each digital interaction is with a verified and trusted source. Mobile applications, equipped with heightened security features, actively monitor and protect user interactions.
Educating clients about the chosen onboarding platform enhances their ability to engage safely and securely, seamlessly complementing the technological defenses. The ability to customise these tools and educational efforts to specific industry requirements further strengthens this comprehensive approach, with seamless integration into the arsenal of tools to safeguard digital interactions against a range of potential threats.
Interested in boosting your monitoring, so you can avoid threats and scams? Book a demo with Checkboard today.


